Review a copy of your credit report at least once each year. First file the theft with the Federal Trade Commission FTC and receive an identity theft affidavit which you will then take when you file the crime with the local police and get a police report.
However these have some limitations in the m-commerce.

. The University of Glamorgan and is currently working towards a PhD in Data. Compare Identity Theft Protection Reviews. All Major Categories Covered.
Identity theft has swiftly become a serious issue for victims police and prosecutors and is a problem that is requiring an increased commitment of resources by private enterprise. Shred any documents with personal or financial information on them. Ad Data Brokers Profit from Your Personal Information.
Guard Against Breaches of Lost or Stolen Credentials with Password Protection. Online ID theft techniques investigation and response 77. These techniques are listed under three headings.
Mining of Intrusion Detection Systems. Ad Best Identity Theft Protection Services 2022. Ad Improve Visibility and Control Access with Adaptive Policies Based on Contextual Factors.
Get Live Support Protect Your Privacy with OneRep. The threat of identity theft is on the rise. Identity thieves often obtain your personal information by outright theft stealing your wallet or purse.
Strategies and Techniques Page 3 When a non-union employer or its agent security officer human resource representative supervisor or manager etc conducts. See our ID Protection Reviews Find Who Is Rated 1. Online organisations commonly use electronic commerce approaches.
A government-issued ID with a photo. 2 Identity theft has swiftly become a serious issue for victims police and prosecutors and is a. Advantage Business Equipment - Check Signing Software Machines.
The ID Theft investigation framework disti nguishes the examination in the victims and the. Fraudsters side and the first level of this investigati on process analysis was hence presented. Get Automated Removal From 100 Sites.
Proof of your address mortgage statement rental agreement or utilities bill Any other proof you have of the theftbills Internal Revenue. Examples of how stolen personal information can be used to. Get Protection from Identity Theft.
Plans for Families Individuals. Notify the credit bureau in writing of any questionable entries. Find Your New Job Today.
Online ID theft techniques investigation and response 77. Ad Check Signing Software Machines Industrial Shredders and more. And 3 social engineering.
This paper presents an evaluation of the. As technology advances so do the techniques used by identity thieves. Here are seven common methods of identity theft.
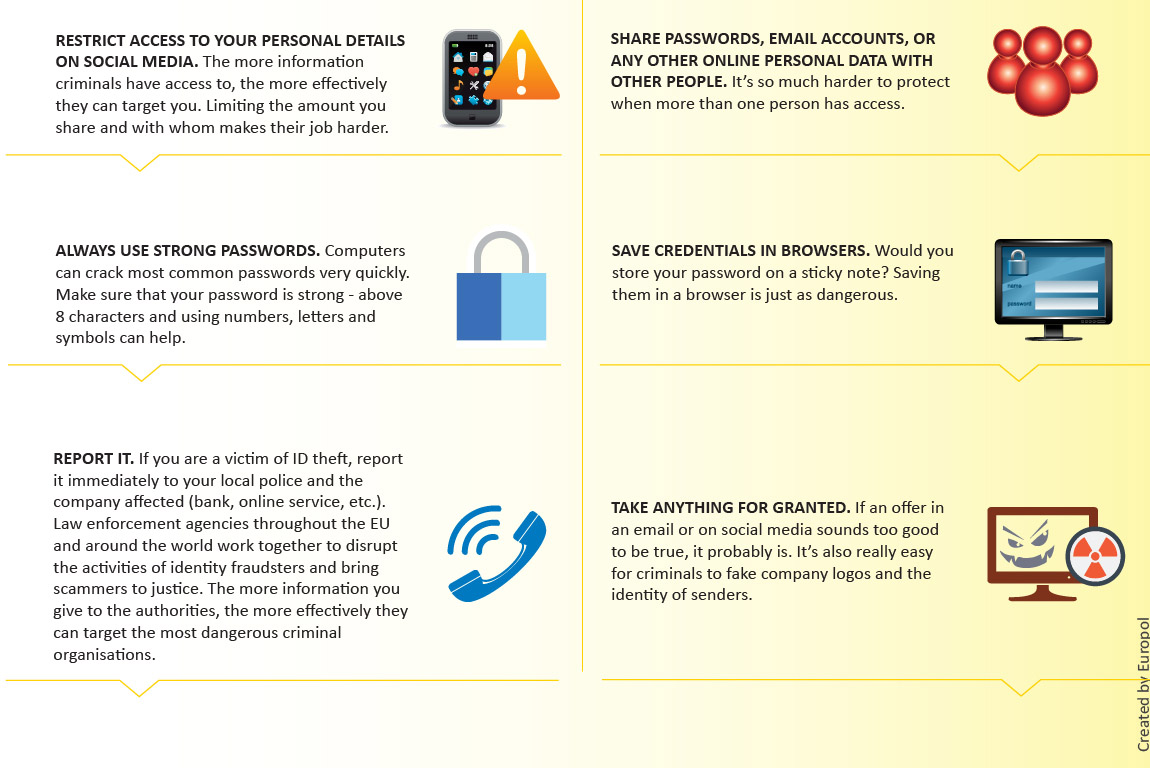
Tips And Advice To Prevent Identity Theft Happening To You Europol

Pdf Identity Theft Identity Fraud And Or Identity Related Crime

Pdf Online Id Theft Techniques Investigation And Response

Calameo Identity Theft Protect Your Identity Online

Tips And Advice To Prevent Identity Theft Happening To You Europol


0 comments
Post a Comment